We’re serious about security.
We’re serious about security.
We understand that the confidentiality, integrity, and availability of your data is vital. Over 10,000 companies trust us to keep their information safe.
Secure culture
Organizational best practices and standards
Organizational best practices and standards
We ensure secure operations and a culture of security awareness through:
- Mandatory background checks, security training, and education for all team members
- Regulatory compliance standards for service providers and partners
- Clear separation of duties to reduce human error and manage risk
Secure operations
A coordinated approach to accreditation and assessment
A coordinated approach to accreditation and assessment
As the security landscape continues to evolve, you can expect us to stay ahead of the threats. Our approach includes:
- A dedicated Security and Compliance team
- 24x7x365 continuous live monitoring and reporting
- Proactive risk assessments and coordinated response to threats
![]()
![]()
Our products meet global compliance requirements including:
- SSAE 118 and ISAE 3402
- ISO 27001 :2013
- General Data Protection Regulation (GDPR)
- Cloud Security Alliance (CSA)
- California Consumer Privacy Act (CCPA)
- Federal Information Security Modernization Act (FISMA)
- Family Education Rights and Privacy Act
Secure environment
Protection against physical intrusion
Protection against physical intrusion
We partner with cloud infrastructure providers like Amazon Web Services (AWS), Microsoft Azure, and others, who provide:
- State-of-the-art data centers housed in nondescript facilities
- Video surveillance, intrusion detection systems, and other electronic monitoring and perimeter control
- Regularly audited physical access logs
- Commercially reasonable efforts to provide a global average up-time of at least 99.99%*
*See Amazon’s Compute Service Level Agreement for more information.
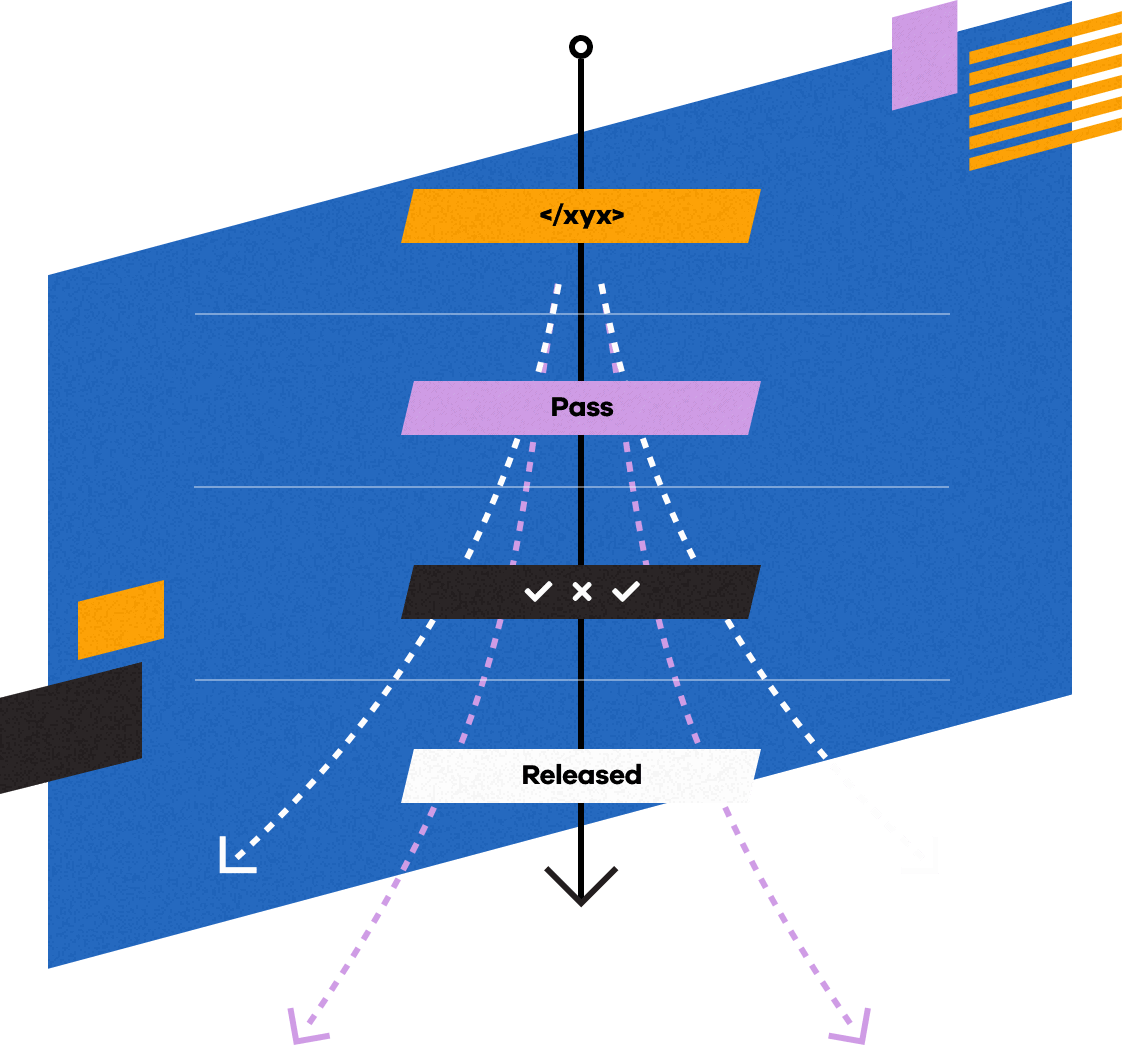
Secure product development
A fully fortified development lifecycle
A fully fortified development lifecycle
Security procedures are built into every stage of our product development efforts, including:
- Automated source code scans of new or modified code
- Standardized, manually run quality assurance testing
- Segmented application servers that accept only legitimate programming requests
- Third-party security assessments prior to every release
Secure infrastructure
A defense-in-depth strategy to enable SaaS
A defense-in-depth strategy to enable SaaS
Our cloud-based infrastructure provides high resiliency, scalability, and true multi-tenant service, protected by several layers of network-based security controls, including:
- Host-based firewalls
- Intrusion detection systems
- Load balancers
- Virtual firewall